Basic concepts of Cryptography
Ever notice that little padlock icon in your browser's address bar? That's cryptography working silently in the background, protecting everything you do online. Whether you're sending an email, making an online payment, or accessing a secured server, cryptographic principles are constantly working to keep your data safe.
Cryptography is the practice of securing communication in the presence of third parties. It's a cornerstone of digital security, allowing us to protect sensitive information even when it's sent across insecure channels like the internet.
This tutorial will walk you through the fundamental concepts and techniques in cryptography, from the basics to more advanced topics.
Why Cryptography Matters
At its core, cryptography ensures:
- Confidentiality: Information is only accessible to those authorized.
- Integrity: Data has not been altered or tampered with.
- Authentication: Verifies the identity of the sender or receiver.
- Non-repudiation: Prevents someone from denying their involvement in a communication or transaction.
Without these protections, every message you send could be read, every transaction altered, and anyone could pretend to be you online.
Meet Alice, Bob, and Trudy
Cryptography scenarios often involve three fictional characters:
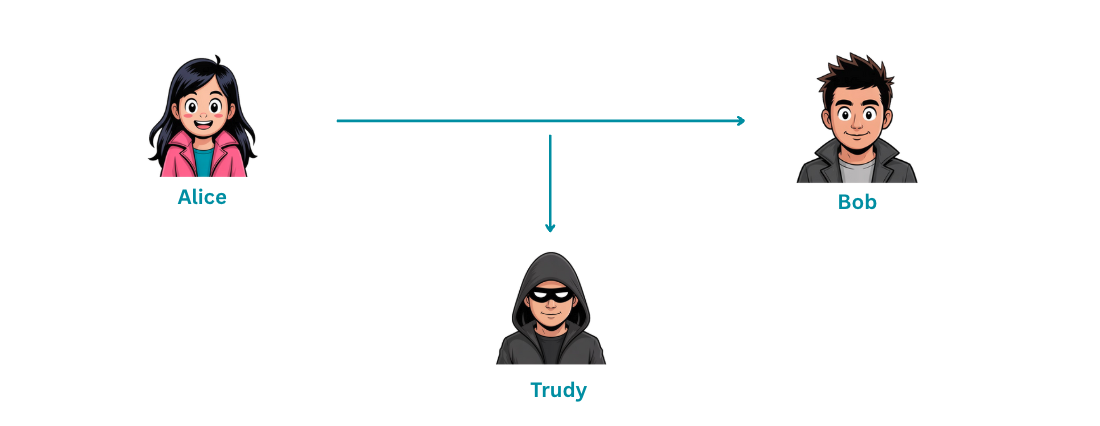
- Alice: The sender of a message.
- Bob: The intended recipient.
- Trudy (the intruder): The malicious third party trying to intercept, modify, or impersonate communications between Alice and Bob.
These characters help us visualize the roles and threats in a cryptographic system. Throughout this guide, we'll see how different cryptographic techniques protect Alice and Bob from Trudy's attacks.
Basic Cryptographic Terminology
Here are some key terms you'll encounter:
| Term | Description |
|---|---|
| Plaintext | The original readable message (e.g., "Hello, Bob!"). |
| Ciphertext | The encrypted message that appears unreadable (e.g., "5A2B1C..."). |
| Encryption | The process of converting plaintext into ciphertext. |
| Decryption | Converting ciphertext back into plaintext. |
| Key | A piece of information used in encryption/decryption. |
| Keyspace | The total number of possible keys that can be used with a particular encryption algorithm. A larger keyspace makes brute-force attacks exponentially harder. |
| Algorithm | The procedure used for encryption and decryption. |
| Key Exchange | The method by which cryptographic keys are securely shared. |
| Digital Signature | A cryptographic code that verifies the authenticity and integrity of a message. |
| Certificate | A digital document used to prove ownership of a public key. |
Symmetric Key Cryptography (Secret Key Cryptography)
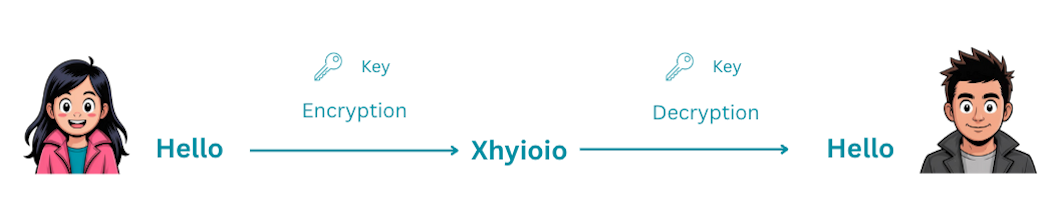
Symmetric encryption uses the same key for both encryption and decryption. Think of it like a traditional lock and key - the same key locks and unlocks the door.
How it Works
- Alice and Bob agree on a secret key
- Alice encrypts her message using this key
- Alice sends the ciphertext to Bob
- Bob decrypts the ciphertext using the same key
Example
Alice wants to send the message "Hi Bob, I'm Alice" to Bob. Here's what happens:
| Item | Value |
|---|---|
| Plain text | Hi Bob, I'm Alice |
| Symmetric Key | SecretK3Y |
| Cipher text | 3c6e0b8a9c1522 |
The process:
- They share a secret key: "SecretK3Y"
- Alice uses the key to encrypt: "Hi Bob, I'm Alice" → "3c6e0b8a9c1522"
- Alice sends "3c6e0b8a9c1522" to Bob
- Bob uses "SecretK3Y" to decrypt "3c6e0b8a9c1522" → "Hi Bob, I'm Alice"
If Trudy intercepts the message, she sees only "3c6e0b8a9c1522" which is meaningless without the key. Even if she tries every possible combination to crack it, a strong key with a large keyspace would take millions of years to break.
Advantages
- Fast and efficient for large amounts of data
- Relatively simple implementation
- Low computational overhead
Disadvantages
- Key distribution problem: How do Alice and Bob securely share the initial key? If they meet in person, it's easy. But if they're on opposite sides of the world and have never met, how do they exchange the key without Trudy intercepting it?
- Scalability issues: Need a unique key for each pair of communicating parties. In a network of 100 people, you'd need 4,950 different keys!
Common Algorithms
- AES (Advanced Encryption Standard): The current gold standard for symmetric encryption
- DES (Data Encryption Standard): Now considered insecure due to small key size
- 3DES: An improvement over DES, but slower than AES
- Blowfish and Twofish: Fast alternatives to AES
Real-World Uses
- Encrypting files on your hard drive
- Database encryption
- VPN tunnels (after key exchange)
- Encrypting data at rest
Asymmetric Key Cryptography (Public Key Cryptography)
Asymmetric encryption solves the key distribution problem by using two mathematically related keys: a public key and a private key. This is the breakthrough that made modern internet security possible.
How it Works
- Bob generates a key pair: public key and private key
- Bob shares his public key openly (even Trudy can have it!)
- Bob keeps his private key secret
- Alice encrypts her message using Bob's public key
- Alice sends the ciphertext to Bob
- Only Bob's private key can decrypt the message
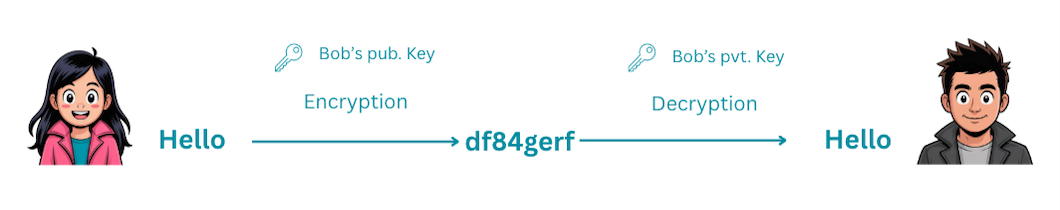
The magic here is that the public key can only encrypt, and the private key can only decrypt. You can't work backwards from the public key to figure out the private key.
Example
| Item | Value |
|---|---|
| Plain text | Hi Bob, I'm Alice |
| Alice Pvt. Key | AlicePvtK3Y |
| Alice Pub. Key | AlicePubK3Y |
| Bob Pvt. Key | BobPvtK3Y |
| Bob Pub. Key | BobPubK3Y |
| Cipher text | caf8e34be07426ae7127c1b4829983c1 |
The process:
- Bob generates key pair: Public key "BobPubK3y" and Private key "BobPvtK3y"
- Bob shares "BobPubK3y" with everyone, including Alice and Trudy
- Alice encrypts "Hi Bob, I'm Alice" using "BobPubK3y" → "caf8e34be07426ae7127c1b4829983c1"
- Alice sends "caf8e34be07426ae7127c1b4829983c1" to Bob
- Bob decrypts using his private key "BobPvtK3y" → "Hi Bob, I'm Alice"
Even if Trudy has Bob's public key and intercepts the encrypted message, she cannot decrypt it without Bob's private key. This is what makes asymmetric encryption so powerful.
Advantages
- Solves the key distribution problem
- Enables secure communication without prior secret sharing
- Enables digital signatures (we'll discuss this next)
- Scales better: everyone just needs one key pair
Disadvantages
- Much slower than symmetric encryption (often 100-1000x slower)
- Requires more computational resources
- Not practical for encrypting large amounts of data
Common Algorithms
- RSA (Rivest–Shamir–Adleman): The most widely used asymmetric algorithm
- ECC (Elliptic Curve Cryptography): Provides same security as RSA with smaller keys
- Diffie-Hellman: Primarily used for key exchange
Real-World Uses
- SSH keys for secure server access
- Email encryption (PGP/GPG)
- SSL/TLS handshakes
- Code signing
- Cryptocurrency wallets
Digital Signatures
Digital signatures solve a different problem: how can Bob verify that a message really came from Alice and wasn't tampered with? This is where we flip asymmetric cryptography around.
How it Works
Instead of encrypting with the recipient's public key, Alice encrypts (signs) with her own private key:
- Alice writes a message
- Alice creates a hash of the message (we'll cover hashing next)
- Alice encrypts the hash using her private key - this is the signature
- Alice sends both the message and the signature to Bob
- Bob decrypts the signature using Alice's public key, revealing the hash
- Bob creates his own hash of the received message
- If the two hashes match, Bob knows the message is authentic and unaltered
Why This Works
- Only Alice has her private key, so only Alice could have created that signature
- If Trudy modifies the message, the hash won't match
- If Trudy tries to create a new signature, she can't without Alice's private key
Example
Alice wants to sign a contract:
| Item | Value |
|---|---|
| Message | "I agree to the terms" |
| Message Hash | 8f3d9e2a... |
| Signature (hash encrypted with Alice's private key) | x7k2m9p4... |
Bob receives the message and signature. He:
- Decrypts the signature using Alice's public key → 8f3d9e2a...
- Hashes the received message → 8f3d9e2a...
- They match! The message is authentic.
Real-World Uses
- Code signing (verifying software hasn't been tampered with)
- Email signatures
- Document signing
- Blockchain transactions
- Software updates
Hash Functions
Hashing is a one-way function that converts data of any size to a fixed-size string. Unlike encryption, you can't reverse a hash to get the original data back.
Properties of Secure Hash Functions
- One-way function: Easy to compute the hash, but impossible to derive the original input from the hash
- Deterministic: The same input always produces the same hash
- Avalanche effect: Small changes in input create large changes in the hash
- Collision resistance: Difficult to find two different inputs that produce the same hash
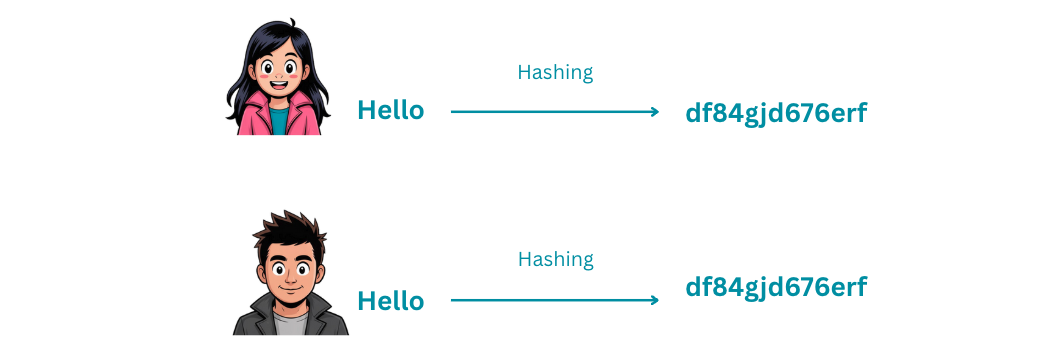
The Avalanche Effect in Action
Let's see how even tiny changes dramatically alter the hash:
Input: "Hello World"
SHA-256: a591a6d40bf420404a011733cfb7b190d62c65bf0bcda32b57b277d9ad9f146e
Input: "Hello World!" (just added an exclamation mark)
SHA-256: 7f83b1657ff1fc53b92dc18148a1d65dfc2d4b1fa3d677284addd200126d9069
Input: "hello world" (just changed H to lowercase)
SHA-256: b94d27b9934d3e08a52e52d7da7dabfac484efe37a5380ee9088f7ace2efcde9Notice how completely different the hashes are? This is the avalanche effect in action. If Trudy changes even one character in a document, Bob will immediately know it's been tampered with.
Uses of Hashing
- Data integrity: Verify that data hasn't been altered during transmission
- Password storage: Store hash of passwords rather than actual passwords
- Digital signatures: Sign hash of a document rather than the entire document (much faster)
- Blockchain: Each block contains the hash of the previous block
- File verification: Download sites provide hashes so you can verify your download wasn't corrupted
Example
Alice wants to ensure the integrity of a document she's sending to Bob:
- Alice calculates the hash of her document: "Important contract" → "5f4dcc3b5aa765d61d8327deb882cf99"
- Alice sends both the document and the hash to Bob
- Bob calculates the hash of the received document
- If Bob's calculated hash matches the hash Alice sent, the document is intact
If Trudy intercepts and modifies the document, the hash Bob calculates won't match the hash Alice sent. Trudy could try to send a new hash, but if Alice signed the original hash with her private key (digital signature), Trudy can't forge it.
Common Hash Algorithms
- SHA-256 (Secure Hash Algorithm): Part of the SHA-2 family, widely used and secure
- SHA-3: The latest standard, designed as an alternative to SHA-2
- MD5 (Message Digest Algorithm): Now considered insecure and broken - do not use for security
- BLAKE2: Fast and secure alternative to SHA-2
- Argon2: Specifically designed for password hashing with built-in resistance to brute-force attacks
Why MD5 is Insecure
MD5 was once popular, but researchers found ways to create different inputs that produce the same hash (collisions). This means Trudy could create a malicious document that has the same hash as a legitimate one. Always use SHA-256 or better for security purposes.
Hybrid Cryptography: Best of Both Worlds
Now here's the clever part. In real-world systems, we don't choose between symmetric and asymmetric encryption - we use both! This is called hybrid cryptography, and it's how HTTPS/TLS actually works.
How it Works
- Asymmetric encryption is used to securely exchange a symmetric key (solves the key distribution problem)
- Symmetric encryption is used for the actual data transmission (fast and efficient)
Example: How HTTPS Works
When you connect to a website over HTTPS:
- Your browser gets the server's public key from its certificate
- Your browser generates a random symmetric session key
- Your browser encrypts this session key using the server's public key
- The server decrypts the session key using its private key
- Now both sides have the same symmetric key
- All subsequent data is encrypted using fast symmetric encryption with this session key
This combines the security of asymmetric encryption with the speed of symmetric encryption. Smart, right?
Why This Matters
- Asymmetric encryption is too slow to encrypt all your web traffic
- Symmetric encryption alone can't solve the key exchange problem
- Together, they give us secure and fast communication
Public Key Infrastructure (PKI)
We've covered how asymmetric encryption works, but there's still one problem: How does Alice know that the public key she received really belongs to Bob? What if Trudy intercepts Bob's public key and replaces it with her own? This is called a man-in-the-middle attack.
This is where Public Key Infrastructure (PKI) comes in.
Certificate Authorities (CAs)
Certificate Authorities are trusted third parties that issue digital certificates verifying the ownership of public keys. Think of them like a government issuing passports - everyone trusts the government to verify identities.
What's in a Certificate?
A digital certificate contains:
- The owner's name (or domain name for websites)
- The owner's public key
- The issuer (which CA issued it)
- Validity period (start and end dates)
- Serial number
- Digital signature from the CA
How it Works
- Bob wants a certificate for his website
- Bob generates a key pair and creates a Certificate Signing Request (CSR)
- Bob sends the CSR to a Certificate Authority (CA)
- The CA verifies Bob's identity (ownership of the domain, business registration, etc.)
- The CA creates a certificate binding Bob's identity to his public key
- The CA signs the certificate with its own private key
- When Alice visits Bob's website, she receives the certificate
- Alice's browser verifies the certificate using the CA's public key (which is pre-installed in her browser)
- If the signature is valid and the certificate hasn't expired, Alice can trust that the public key belongs to Bob
Certificate Chains and Root CAs
In practice, there are multiple levels of CAs:
- Root CAs: The ultimate trusted authorities (their certificates are pre-installed in your browser/OS)
- Intermediate CAs: Issued by root CAs, they issue certificates to end users
- End-entity certificates: The certificate Bob gets for his website
This creates a "chain of trust" from your website certificate up to a root CA.
What Happens When Things Go Wrong?
- Expired certificate: The validity period has passed, browser shows a warning
- Revoked certificate: The CA has invalidated the certificate (maybe the private key was compromised)
- Self-signed certificate: A certificate not signed by a trusted CA - browsers will warn you
- Wrong domain: Certificate is for different domain than the one you're visiting
Real-World Example: HTTPS
When you visit https://example.com:
- The server sends its certificate
- Your browser checks: Is it signed by a trusted CA? Is it expired? Is the domain correct?
- Your browser verifies the CA's signature using the CA's public key
- If everything checks out, you see the padlock icon
- If something's wrong, you see a security warning
This is PKI in action, protecting you from man-in-the-middle attacks every time you browse the web.
Common Attacks and How Cryptography Defends Against Them
Let's look at what Trudy might actually try and how our cryptographic tools protect against her.
Man-in-the-Middle Attack
The Attack: Trudy intercepts communication between Alice and Bob, reading and possibly modifying messages.
Defense:
- PKI and certificates ensure Alice is really talking to Bob
- Digital signatures detect any message modifications
- TLS/HTTPS protects against this in web browsing
Brute Force Attack
The Attack: Trudy tries every possible key until she finds the right one.
Defense:
- Large keyspace makes this impractical
- AES-256 has 2^256 possible keys - trying them all would take longer than the age of the universe
- This is why key length matters!
Replay Attack
The Attack: Trudy records a valid encrypted message and sends it again later (e.g., "transfer $1000 to Trudy" repeated multiple times).
Defense:
- Include timestamps in messages
- Use nonces (numbers used only once)
- Sequence numbers ensure messages are processed in order
Password Cracking
The Attack: Trudy steals a database of password hashes and tries to crack them.
Defense:
- Use strong hash functions designed for passwords (Argon2, bcrypt)
- Add "salt" (random data) to each password before hashing
- Makes rainbow tables (pre-computed hash databases) useless
Collision Attack
The Attack: Trudy finds two different inputs that produce the same hash.
Defense:
- Use collision-resistant hash functions (SHA-256, not MD5)
- Modern hash functions make finding collisions computationally infeasible
Quick Comparison: Symmetric vs Asymmetric
| Feature | Symmetric | Asymmetric |
|---|---|---|
| Keys | One shared key | Key pair (public + private) |
| Speed | Very fast | Much slower (100-1000x) |
| Key Distribution | Difficult | Easy |
| Use Case | Bulk data encryption | Key exchange, signatures |
| Key Length | 128-256 bits typical | 2048-4096 bits typical |
| Examples | AES, 3DES | RSA, ECC |
| Real-World Use | File encryption, VPNs | HTTPS, SSH, Email signing |
Common Misconceptions
"Encryption makes data 100% secure"
Not quite. Encryption is extremely strong when implemented correctly, but security involves more than just encryption. Weak passwords, software vulnerabilities, phishing attacks, and human errors can all compromise security even with strong encryption in place.
"Longer passwords are always better"
Not always. "p@ssw0rd123456789" is long but weak because it's based on a dictionary word with common substitutions. "correct-horse-battery-staple" is both long and strong because it's random words. Length helps, but randomness and unpredictability matter more.
"HTTPS means the website is trustworthy"
HTTPS only means the connection is encrypted and you're talking to the server that owns that domain. A scam website can have a valid HTTPS certificate. Always check the domain name carefully!
"I can't break the encryption, so I'm safe"
Attackers rarely try to break modern encryption directly. Instead, they:
- Exploit software bugs
- Use phishing to steal passwords
- Compromise systems before data is encrypted
- Attack the endpoints, not the encryption
Practical Applications Summary
Here's where you'll find these cryptographic concepts in real life:
Symmetric Encryption:
- Full disk encryption (BitLocker, FileVault)
- Database encryption
- Encrypted file containers
- VPN data tunnels
Asymmetric Encryption:
- SSH keys for server access
- PGP/GPG email encryption
- Code signing
- SSL/TLS handshakes
- Bitcoin and cryptocurrency
Hashing:
- Password storage
- Blockchain
- File integrity verification (checksums)
- Git commit identifiers
- Digital forensics
Digital Signatures:
- Software updates (verifying authenticity)
- Email signatures
- PDF document signing
- Legal documents
- Smart contracts
PKI/Certificates:
- HTTPS websites
- Email encryption (S/MIME)
- VPN authentication
- Code signing certificates
What's Next?
Cryptography is constantly evolving. Here are some emerging topics worth exploring:
Post-Quantum Cryptography: Current asymmetric algorithms (RSA, ECC) could be broken by quantum computers. Researchers are developing new algorithms that resist quantum attacks.
Zero-Knowledge Proofs: Prove you know something without revealing what you know. Used in privacy-focused cryptocurrencies.
Homomorphic Encryption: Perform computations on encrypted data without decrypting it first. Imagine searching encrypted emails or processing encrypted medical records.
Blockchain and Distributed Trust: Moving beyond traditional certificate authorities to decentralized trust models.
Final Thoughts
Cryptography is what makes the modern internet possible. Every secure connection, every digital signature, every encrypted message relies on these fundamental principles. While the math behind it can get complex, the concepts are straightforward: protect confidentiality, ensure integrity, verify authenticity, and prevent repudiation.
The next time you see that little padlock icon, you'll know exactly what's happening behind the scenes: asymmetric encryption exchanging keys, symmetric encryption protecting your data, hash functions ensuring integrity, and PKI certificates establishing trust. All working together to keep you safe online.
Quick Reference Guide
Key Terms
| Term | Description |
|---|---|
| Plaintext | Original readable message |
| Ciphertext | Encrypted, unreadable message |
| Encryption | Converting plaintext to ciphertext |
| Decryption | Converting ciphertext back to plaintext |
| Key | Secret information used in encryption/decryption |
| Keyspace | Total number of possible keys (larger = more secure) |
| Algorithm | The encryption/decryption procedure |
| Key Exchange | Securely sharing cryptographic keys |
| Digital Signature | Cryptographic proof of authenticity and integrity |
| Certificate | Digital document proving public key ownership |
| Hash | One-way function producing fixed-size output |
| Salt | Random data added to passwords before hashing |
| CA | Certificate Authority - issues and verifies certificates |
| PKI | Public Key Infrastructure - system for managing certificates |
| TLS/SSL | Protocols for secure internet communication |
Algorithm Cheat Sheet
Symmetric (Fast, Shared Key):
- AES-256: Current standard
- ChaCha20: Modern alternative to AES
- 3DES: Legacy, avoid for new projects
Asymmetric (Slow, Key Pairs):
- RSA-2048/4096: Widely supported
- ECC: Smaller keys, same security
- Ed25519: Modern, fast signing
Hashing (One-way):
- SHA-256: General purpose
- SHA-3: Alternative to SHA-2
- Argon2: Password hashing
- BLAKE2: Fast alternative
Key Exchange:
- Diffie-Hellman: Classic key exchange
- ECDH: Modern, efficient
- RSA key exchange: Common in TLS